As of the most recent 2020.2, Google OpenID SSO is deprecated and no longer available to NetSuite users. Users should also be aware that with the upcoming 2021.1 release, the NetSuite proprietary Inbound SSO feature is targeted for deprecation. Partners and customers with solutions based on these features must update these solutions to use an alternative inbound single sign-on feature.
Luckily, OpenID Connect (OIDC) SSO and SAML SSO provide alternatives for inbound SSO access to NetSuite UI and Commerce websites.
Important: Before the NetSuite proprietary Inbound SSO feature becomes deprecated, you can disable the feature for testing purposes. You can disable and re-enable the feature at any time. To temporarily disable the Inbound SSO feature, go to Setup > Company > Setup Tasks > Enable Features. On the SuiteCloud subtab, check the Disable Inbound Single Sign-on box.
The SOAP web services ssoLogin operation is part of the proprietary Inbound SSO feature. To avoid issues after this feature is deprecated, you must update your integrations that use the ssoLogin operation to use Token-based Authentication (TBA).
OpenID Connect (OIDC) Single Sign-on
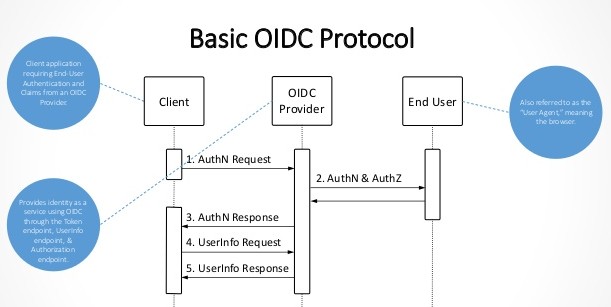
The OpenID Connect (OIDC) Single Sign-on feature provides several benefits for user access to the NetSuite UI and a web store. If the OIDC configuration is shared between different NetSuite accounts, users can switch between OpenID Connect (OIDC) Single Sign-on roles without requiring a separate login. User credentials and policies are managed by the OIDC provider (OP). NetSuite is the client, or relying party (RP).
OpenID Connect (OIDC) Single Sign-on is an alternative to other single sign-on (SSO) methods currently available in NetSuite: SAML SSO, Google OpenID SSO, and the NetSuite proprietary version of Inbound SSO. OIDC is an identity layer on top of the OAuth 2.0 protocol. OIDC uses JavaScript Object Notation (JSON) as the data format and uses JSON Web Tokens (JWT) to transfer claims between parties.
To implement OpenID Connect Single Sign-on to NetSuite:
- Choose a vendor, an OpenID Connect Provider (OP), and register NetSuite with your OP as the client, or relying party (RP).
- Click the link in each of the following steps for information on how to complete the setup for the OpenID Connect (OIDC) feature in NetSuite:
- Enable the OpenID Connect (OIDC) Single Sign-on Feature in NetSuite.
- Go to Setup > Company > Setup Tasks > Enable Features and click the SuiteCloud subtab.
- In the Manage Authentication section, check the OpenID Connect (OIDC) Single Sign-on box. Click I Agree on the SuiteCloud Terms of Service when prompted.
- Click Save.
- Configure OpenID Connect (OIDC) in NetSuite.
- Go to Setup > Integration > Manage Authentication > OpenID Connect (OIDC) Single Sign-on.
- Enter the Client ID you obtained from your OP.
- Enter the Client Secret you obtained from your OP.
- (Optional) Enter the Post Logout Redirect URL as a valid URL value.
- (Optional) Enter the Allowed Email Domains as comma-separated values.
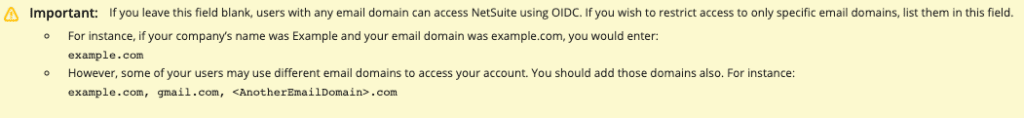
- The Set Configuration From URL option is selected by default. Enter the Configuration URL you obtained from your OP.
- Click Submit.
- Customize Roles for OpenID Connect and add OpenID Connect Permissions.
- Go to Setup > Users/Roles > User Management > Manage Roles.
- Choose a role and click Customize.
- Create a unique and identifiable name for the role. For example, you could replace the word Customize in the role name with the OIDC.
- Click the Permissions tab.
- On the Setup subtab, select the appropriate OIDC permission from the list, and click Add. There are two OIDC permissions:
- Set Up OpenID Connect (OIDC) Single Sign-on
- OpenID Connect (OIDC) Single Sign-on
- Click Save.
- Assign the OpenID Connect Single Sign-on Role to Users.
- Find the appropriate entity record for the user. For an employee, go to Lists > Employees > Employees.
- Click the name of the user and Edit.
- Navigate to the Access subtab.
- On the Roles subtab, select your custom OpenID Connect role from the list.
- Click Add.
- Click Save.
- Tell your users how to access NetSuite using OpenID Connect. See User Access to NetSuite with OpenID Connect.
- Most users will access NetSuite with OpenID Connect one of two ways:
- On the portal of the OpenID Connect Provider (OP), select NetSuite. Users are redirected to the NetSuite Change Role page.
- On the first login attempt, from an account-specific domain URL in the following format: https://<accountID>.app.netsuite.com/app/login/secure/oidc.nl where <accountID> is a variable representing the NetSuite account ID. When the OIDC configuration has been completed for an account, the user is redirected to the OP’s login form. The user enters the OP login credentials and is redirected to the Choose Role page in NetSuite.
- Most users will access NetSuite with OpenID Connect one of two ways:
- Enable the OpenID Connect (OIDC) Single Sign-on Feature in NetSuite.
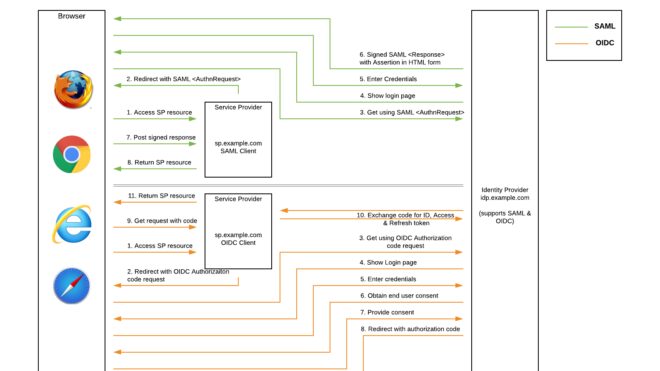
SAML Single Sign-on
SAML (Security Assertion Markup Language) is an XML-based standard that supports communication of user data among different enterprise applications, called service providers (SPs). An identity provider (IdP) makes security assertions consumed by other service providers. A single IdP can perform user authentication for many SPs. A particular SP and an IdP can establish a circle of trust by providing each other with metadata in an XML format defined by SAML specifications so that the SP accepts users authenticated by the IdP.
The NetSuite SAML Single Sign-on feature is based on the Security Assertion Markup Language (SAML) v2.0 specifications. Any SAML 2.0-compliant application can serve as the IdP for SAML access to NetSuite.
The SAML Single Sign-on (SSO) feature supports inbound single sign-on access to NetSuite using authentication from a third-party IdP. This feature allows users who have logged in to an external application to go directly to NetSuite. Users do not need to log in separately to NetSuite, because authentication from the same IdP is used for log in to both the external application and NetSuite. A user who accesses NetSuite using SAML SSO is directed to their NetSuite Home page. NetSuite account administrators can use role-based permissions in NetSuite to control which users have SAML SSO access to NetSuite.
To enable the SAML Single Sign-on feature:
- Go to Setup > Company > Setup Tasks > Enable Features and click the SuiteCloud subtab.
- In the Manage Authentication section, check the SAML Single Sign-on box. Agree to the SuiteCloud Terms of Service when prompted.
- Click Save.
To add SAML Single Sign-on Permissions to Roles
- Go to Setup > Users/Roles > User Management > Manage Roles.
- Choose a role and click Customize.
- Create a unique and identifiable name for the role. For example, you could replace the word Customize in the role name with the word SAML.
- Click the Permissions tab.
- On the Setup subtab, select the appropriate SAML permission from the list, and click Add. There are two SAML permissions. Add one or both permissions to the role as appropriate.
- Click Save.
To add the SAML Single Sign-on permission to a customized center role:
- Go to Setup > Users/Roles > User Management > Manage Roles.
- Click Edit for a customized center role or click Customize for a standard center role.
- On the Role page, click the Permissions subtab.
- On the Setup subtab, set the Level to Full for the SAML Single Sign-on permission.
To assign a SAML Single Sign-on role to users:
- Find the appropriate entity record for the user. Go to Lists > Employees > Employees.
- Click the name of the user and Edit.
- Navigate to the Access subtab.
- Select your custom SAML Single Sign-on role from the list.
- Click Add.
- Click Save.
To copy the NetSuite SP metadata file and related URL:
- Go to Setup > Integration > Manage Authentication > SAML Single Sign-on (Administrator).
- Copy the URL shown in the NetSuite Service Provider Metadata field, and save it where you can retrieve it when necessary.
- Download the SP metadata file to your computer. Remember the location you save the file to.
To configure SAML with your IdP:
- Go to your IdP website or an on-premises administration console, and follow the application setup instructions from your IdP.
- Provide the NetSuite Service Provider Metadata to your IdP by one of the following methods:
- Upload the NetSuite SP metadata file, or:
- Paste the URL for the NetSuite SP metadata file in the appropriate field with your IdP, or:
- Manually configure SAML on the IdP side by copying information from specific fields in the NetSuite Service Provider Metadata file to the IdP.
Your IdP (website or on-premises console) From the NetSuite Service Provider Metadata file SP Entity ID Always refer to the NetSuite Service Provider Metadata file in your account. Copy the SP entityID from the NetSuite Service Provider metadata file you downloaded from the SAML Setup page your account.
The SP entityID is shown in the first line of the file.
Assertion Consumer Service Always refer to the NetSuite Service Provider Metadata file in your account. Copy the URL from the NetSuite Service Provider metadata file you downloaded from the SAML Setup page in your account.
Important
As of May 2020, the default Assertion Consumer Service refers to the NetSuite system domain:
https://system.netsuite.com/saml2/acs. You do not have to change the configuration if we move your account to a different data center location, or if you configure SAML SSO in multiple accounts in different data center locations.Single Logout Service Always refer to the NetSuite Service Provider Metadata file in your account. Copy the URL from the NetSuite Service Provider metadata file you downloaded from the SAML Setup page in your account.
Important
Use only the value on the first line of the list:
https://system.netsuite.com/saml2/slopostEnsure you use a POST binding.
- Your IdP also has an IdP metadata configuration file. You must copy the URL for this file, or download the IdP metadata file. (Later, you must either enter the URL or upload the file into NetSuite on the SAML Setup page.)
- With your IdP, you must assign (or provision) the NetSuite application to the SAML users in your account.
Defining the NetSuite Configuration for SAML
To support SAML single sign-on access to NetSuite, you must define the following on the SAML Setup page:

- The Logout Landing Page.
- Logout Landing Page – after logging in to NetSuite through SAML single sign-on, this is the URL for a page that users should be redirected to when they log out of NetSuite. An IdP Single Logout page can be specified for Single Logout to work.
- Optionally, the Primary Authentication Method.
-
- By default, the Primary Authentication Method option is not checked. If SAML users click a link to access NetSuite when no active NetSuite session exists, they are redirected to the NetSuite login page. This redirect might cause issues for users who do not know their NetSuite credentials.
- If you check the Primary Authentication Method box, users can be redirected to the external IdP login page. This redirect is available if:
- the user has already been logged in, the redirect occurs based on previous experience with NetSuite.
- the access link includes the NetSuite account ID set as the c or compid URL parameter or as an account-specific domain, formatted like the following:https://system.netsuite.com/app/center/card.nl?c=<ACCOUNTID> or https://<accountID>.app.netsuite.com/app/center/card.nl
- Users will be redirected to the IdP login page upon session timeouts.
Finally, Set Up Your Identity Provider (IdP) in NetSuite
SAML single sign-on access to NetSuite requires that you specify an XML file that defines the identity provider to be used for authentication and includes required metadata for this identity provider. The format of this file must be aligned with SAML v2.0 specifications.
On the SAML Setup page, the IdP metadata file can be specified by entering a URL or by uploading the actual XML file. This is the information you gathered when you were setting up NetSuite with your IdP.
 You must do one of the following:
You must do one of the following:
- Choose Indicate IDP metadata URL and enter the location URL of the metadata file.
- Or, choose the Upload IDP metadata File option and browse to locate the file.